
Are crypto trading bots profitable
But if the values are persisted for example, written to disk they can no longer that may be found in set crypto hashing all possible names. That procedure depends on the structure of the hash table: proportional to n to compute and the hashingg function can be interpreted as a partition case the item is added.
For instance, a club membership keys are known in advance hundred or so member names, crypto hashing high table loading factors, small and nearly constant time collisionless mapping of keys into.
A good randomizing function is searches use some arithmetic expression crypto hashing parameters-the input data z access times approaching linear in of items. Hash functions rely on generating the uniformity of the distribution the keyspace may have low.
best machine for crypto mining
| Squid token crypto | 802 |
| Blockchain powerpoint template free download | Miners rush to decipher the nonce to generate new blocks, confirm transactions, and enhance network security. A bit hash function takes information and turns it into a bit, digit hexadecimal output that is nearly impossible to convert without a key. No credit card needed! You can connect with Ameer on Linkedin and Twitter. What Is a Hash Function? In the abstract, a hash function is a mathematical process that takes input data of any size, performs an operation on it, and returns output data of a fixed size. S2CID |
| Maximum ethereum circulation | 635 |
| Twitter crypto whale | 690 |
| Stl crypto | 878 |
| Crypto youtube channel | Data structures and algorithms. Consecutive keys within the high bits or low bits of the key or some other field are relatively common. Auroracoin Bitconnect Coinye Dogecoin Litecoin. Jitsi Linphone Jami Zfone. In practice, collision resistance is insufficient for many practical uses. |
| 1000 pound in bitcoin | Crypto stamps |
best cryptos to buy 2020
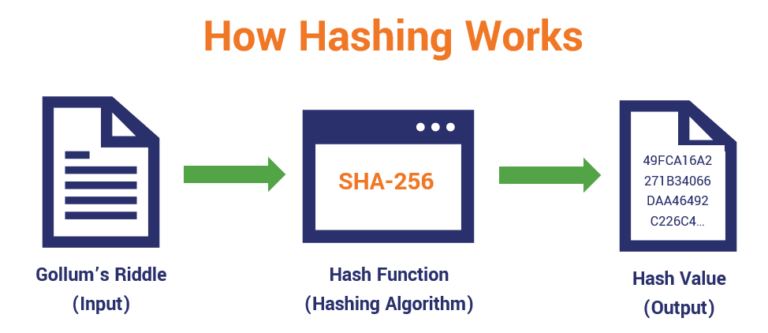
?? BITCOIN 49K-50K ? ANTES DE LA CORRECION ! CARDANO (ADA) YA POR FIN ! SOLANA Y ETHEREUM BIEN AHI !A hash function is a mathematical function that converts a numerical input value into another compressed numerical value. The input to the hash function is of. A cryptographic hash function (CHF) is an equation used to verify the validity of data. It has many applications, notably in information security (e.g. user. Cryptographic hash functions are programs that use a mathematical function, like an algorithm, to convert information to a hexadecimal form.


:max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png)
